What is Tokenization and Why is it so important?
In today's digital-first world, protecting sensitive data is a cornerstone of cybersecurity. Data tokenization stands out as a highly effective way to secure information, providing both robust protection and operational flexibility. So, what is data tokenization, and why is it so important?
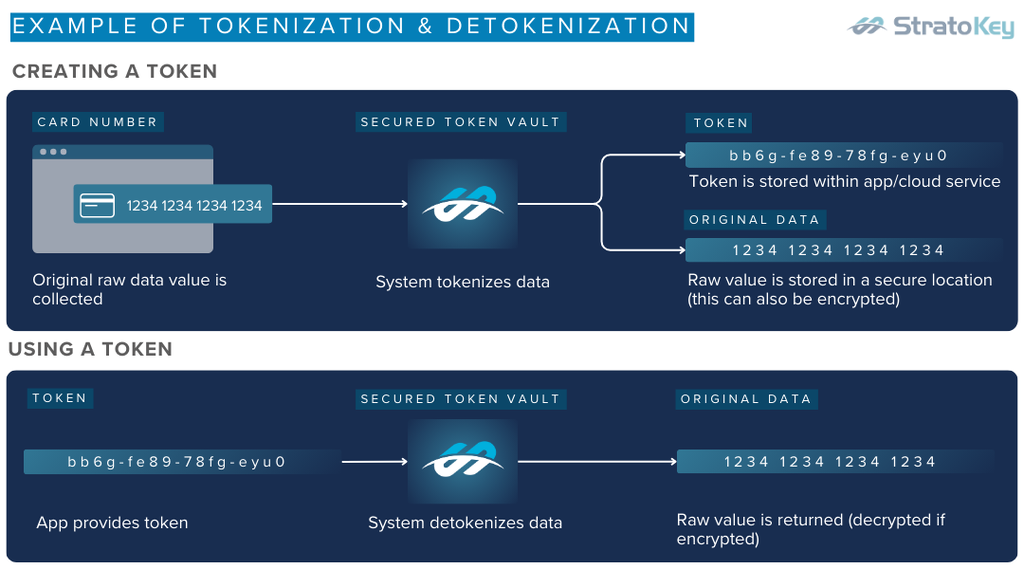
Data tokenization is the process of replacing sensitive or regulated data, like confidential business information, protected heath information (PHI) or personally identifiable information (PII) with a non-sensitive counterpart called a token.
These tokens are meaningless without a token vault that maps them back to the original data. Unlike encryption, which transforms data into secure formats (ciphertext) that are decrypted with keys, tokenization entirely removes the sensitive data from a system, replacing it with a non-sensitive token.
How Does Tokenization Work?
The power of tokenization lies in its simplicity. Sensitive data is identified and replaced with tokens before being stored or shared. These tokens have no exploitable value and the data they represent cannot be derived from the token itself. The mapping of tokens to the original data is securely maintained in an encrypted token vault. This ensures that the data remains inaccessible even if the tokenized data is exposed.
Tokenization Process
Step 1: Identify Sensitive Data
The first step is to determine which data elements require protection. Sensitive information such as CUI, PHI, Social Security numbers, or other PII are often identified to be tokenized.
Step 2: Generate Tokens
Once the sensitive data is identified, a tokenization system generates random tokens to replace it. These tokens can retain the format of the original data (e.g., a 16-digit token for a credit card number) to maintain compatibility with existing systems. The generated tokens are meaningless without the token vault, making them secure even if intercepted.
Step 3: Storing Data in a Token Vault
The original sensitive data is stored securely in a token vault, a centralized database with strict access controls and encryption. This vault contains the mapping between the sensitive data and its corresponding tokens.
Step 4: Using Tokens in Systems
The tokens are used in place of sensitive data within systems such as SaaS applications, databases and workflows.
For example:
- In payment processing, tokens can be passed through systems to authorize transactions without exposing actual credit card numbers.
- In analytics, tokens allow data to be processed without compromising security.
Because tokens do not expose sensitive data, they reduce the risk of breaches and the scope of compliance requirements.
Step 5: Reverse Mapping for Authorized Access
When authorized users or systems need access to the original data, the tokenization system retrieves it from the token vault using the mapping. This access is strictly controlled and logged to ensure accountability and prevent misuse.
Key Features That Enhance Tokenization
- Format-Preserving Tokens: Tokens often mimic the format of the original data, ensuring seamless integration with existing systems.
- Irreversibility: Outside the token vault, tokens cannot be deciphered to gain the original data, even by brute force, as they have no mathematical relationship with the sensitive data.
- Vault Access Controls: Token vaults use encryption, role-based access controls, and auditing to secure sensitive data and ensure compliance.
Key Benefits of Tokenization
Data tokenization offers a wide range of benefits. At its core, tokenization minimizes the risks associated with storing sensitive information, reduces the number of systems that manage sensitive information and helps with compliance across a variety of regulations. These advantages are especially important in industries such as finance, healthcare, aerospace and defense where the stakes for data security are high and often mission critical.
Reducing Data Breach Impacts
One of the most significant advantages of tokenization is its ability to drastically reduce the impact of data breaches. Even if a system is compromised, the stolen tokens are meaningless without access to the secure token vault. This added layer of security safeguards sensitive information from unauthorized access.
Enhanced Regulatory Compliance
Tokenization helps businesses adhere to strict data protection standards such as the Payment Card Industry Data Security Standard (PCI DSS), the Cybersecurity Maturity Model Certification (CMMC) the General Data Protection Regulation (GDPR), and the Health Insurance Portability and Accountability Act (HIPAA). By replacing sensitive data with tokens, companies can reduce the scope of their compliance audits and avoid penalties for non-compliance.
Solution for Data Residency Requirements
Tokenization also plays a pivotal role in addressing data residency requirements. Tokenization enables organizations to store sensitive data locally, keeping the original information within the required region while still allowing the use of tokens globally. This reduces exposure of sensitive data to foreign jurisdictions.
Operational Integrity of Data
Tokenization preserves operational integrity by allowing tokens to retain the format and structure of the original data. This means systems can continue to function without requiring the sensitive information, enabling businesses to process transactions, perform analytics, and deliver customer services securely and efficiently.
Scalability, Interoperability and Integration
Tokenization provides key benefits in scalability, interoperability, and integration. Its mapping of original data to tokens enables organizations to efficiently handle large transaction volumes without compromising security or performance, making it ideal for high-transaction sectors like finance and e-commerce. Additionally, tokenization offers a standardized method for securely exchanging sensitive data across different systems, enhancing interoperability. Many tokenization solution like StratoKey also include APIs or libraries for easy integration with existing IT infrastructure, streamlining adoption and reducing development time. This combination ensures businesses can scale effectively while maintaining strong security measures.
Together, these benefits make data tokenization an invaluable tool for safeguarding sensitive information while supporting compliance and operational objectives.
What Is the Difference Between Data Encryption and Data Tokenization?
Data tokenization and encryption are both techniques for protecting sensitive information, but they differ in their approach and purpose.
Tokenization replaces sensitive data with randomly generated tokens that have no intrinsic value and are stored separately in a secure token vault. It is irreversible without access to the vault, making it ideal for reducing compliance scope and protecting sensitive data.
Encryption, on the other hand, transforms data into unreadable ciphertext using algorithms and keys. It is reversible with the appropriate decryption key and is commonly used to secure large datasets, files, or data in transit. The benefit of encryption is that there is not token vault to protect, with sensitive data being secured and then stored directly in the end system.
Comparison Table: Encryption vs. Tokenization
| Aspect | Data Encryption | Data Tokenization |
| Transformation Method | Uses algorithms to encode data into protected formats (ciphertext). | Replaces sensitive data with random, non-sensitive tokens. |
| Reversibility | Reversible with the correct decryption key. | Irreversible outside of the token vault. |
| Key Dependency | Relies on encryption and decryption keys for security. | Relies on secure token vault for mapping tokens to original data. |
| Use Cases | Ideal for protecting large datasets, files, or communications in transit and at rest. | Best for securing specific sensitive data fields, such as credit card numbers or PII, especially in compliance-focused industries. |
| Compliance Scope | Encryption is often referenced directly in regulatory requirements and data security frameworks. | Tokens are often not considered sensitive data, reducing compliance scope and audit requirements. |
| Risk in Breach Scenario | If the encryption key is compromised, the encrypted data can be decrypted. | Tokens are meaningless without access to the token vault (which is also encrypted), minimizing the impact of a breach. |
Which Security Technique Is Right for Your Organization?
While encryption protects data integrity across systems, tokenization focuses on removing sensitive data entirely from exposed environments. Both techniques are complementary in a layered security strategy and when used together can enhance the overall security posture.
In regards compliance, the appropriate data security technique will depend on the varying regulatory requirements the industry and data is subject to, their interpretation, and approval by auditing and assessment entities.
When selecting security techniques it helps to consider the following:
Security Risks
- Industry vulnerability: Different industries face varying levels of cyber threats. Assessing an industry's risk profile can guide the choice.
- Attack history: A history of attacks may necessitate a more robust and layered security approach.
Data Protection Needs
- Type of data: Identify the specific types of data to protect.
- Data use cases: Determine how the data will be used and if frequent access to the original data is needed.
Cost
- Industry vulnerability: What are the budget constraints and long term investment required?
Compliance Requirements
- Regulatory frameworks: Understand the compliance landscape relevant to the industry and data type.
- Scope reduction: Is there a strong need to reduce the scope of compliance audits?
- Audit requirements: Work with auditors to select the protection strategy to best meet the specific regulatory requirements.
How StratoKey Can Assist With Tokenization and Encryption
StratoKey's intelligent Cloud Access Security Broker (CASB) features a Cloud Data Protection Gateway with a tokenization and encryption engine for popular SaaS and cloud services such as NetSuite, Salesforce, Jira, Confluence, and ServiceNow. Sensitive data is stored in an encrypted database (token vault), whilst the token is provided to the requestor for use.
By utilizing tokenization, organizations can effectively manage the exposure of sensitive information, ensuring that even if tokens are intercepted during transit, they hold no intrinsic value and cannot be reverse-engineered to reveal the original data. Moreover in addition to typical database security, the StratoKey token store makes use of FIPS validated encryption to secure sensitive data prior to being persisted into the token vault. This adds an additional layer of security in addition to standard database encryption.
StratoKey offers comprehensive security features including monitoring, analytics, and access controls through its Encryption (and tokenization), Monitoring, Analytics and Defensive (EMAD™) capabilities. This layered security approach ensures that only authorized personnel in designated locations can access sensitive data.
Since 2012, StratoKey has supported clients across various sectors - including healthcare, banking, financial services, manufacturing, cybersecurity, education, and technology - in meeting their cloud data security needs.
For further information about StratoKey's offerings, please contact us or download the StratoKey White Paper.
- The NIS2 Directive, What You Need To Know
- Oracle Cloud Breach, Reportedly 6 Million Records Exposed
- Encryption of ePHI, a Required Safeguard for HIPAA Compliance
- Why you should host your own Encryption Gateway
- What is Tokenization and Why is it so important?
- Data Residency, What Is It and Why It Is So Important for Global Data Compliance
- GDPR and Encryption
- CASB Guide
- What is a CASB?
- Corporate Australia to 'rethink' Cyber Security Policies with Serious Data Breaches Bill
- StratoKey named finalist at RSA Conference for Most Innovative Company
- Corporate Australia to 'rethink' Cyber Security Policies with Serious Data Breaches Bill
- Encryption of ePHI, a Required Safeguard for HIPAA Compliance
- Oracle Cloud Breach, Reportedly 6 Million Records Exposed
- What is Tokenization and Why is it so important?
- Data Residency, What Is It and Why It Is So Important for Global Data Compliance
- Legal Ramifications of Data Breaches
- The NIS2 Directive, What You Need To Know
- What is a CASB?
- Cloud Access Security Broker Checklist




